Cypherdog Encryption Business
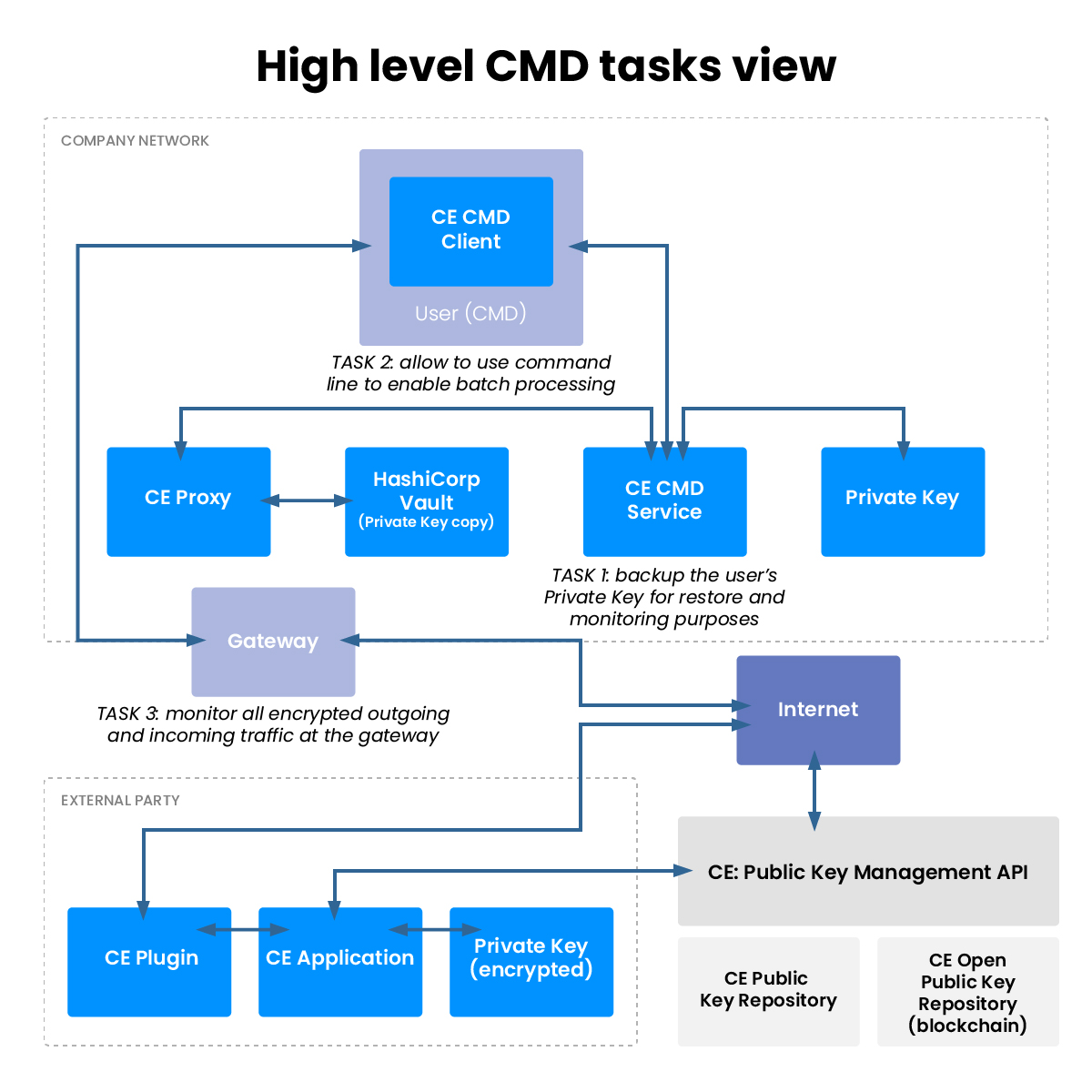
Command Line

Challenges Addressed
- How can we secure confidential documents sent to multiple recipients?
- Ensuring confidentiality in transmitted documents.
- Preventing data leaks and unauthorized disclosure of personal and sensitive data.
- Compliance with NIS-2 and DORA-2 regulations.
Confidential documents containing personal, financial, or sensitive data are typically sent as PDFs or password-protected ZIP archives. However, sending the password in plain text via email or SMS is a significant security risk. This method's limitations include the need for varied and often weak passwords for different recipients, making them susceptible to brute-force or dictionary attacks.
Target Audience
- Financial institutions (banks, insurers)
- Healthcare sector
- Local government entities
- Central administration
- Property managers
- Businesses
Documents to Encrypt
- Confidential financial documents (bank statements, credit card transactions, insurance policies)
- Contract updates
- Fee tables
- Medical diagnostic test results
- Local and central tax amount letters
- Fee schedules
Moving beyond inadequate PDFs or password-protected ZIP files in this era of escalating cyberattacks, Cypherdog offers a solution based on asymmetric encryption without third-party involvement.
Solution Features
- Command-line access for encryption, decryption, and recipient account verification.
- Automation capability for encrypting texts and files.
- Script creation for mass encryption.
- Compatibility with standard email servers and other communication mediums.
- Initial document encryption includes an invitation for recipients to download the decryption application and a one-time password.
- Scalable to meet varying needs.
- Capabilities for machine-to-human and machine-to-machine encryption.
- Monitoring of transmitted encrypted content at the gateway.
- Real end-to-end encryption without third-party involvement.
- Free application for recipients.
- Possible applications for encrypting communications from Customer to Service Provider.