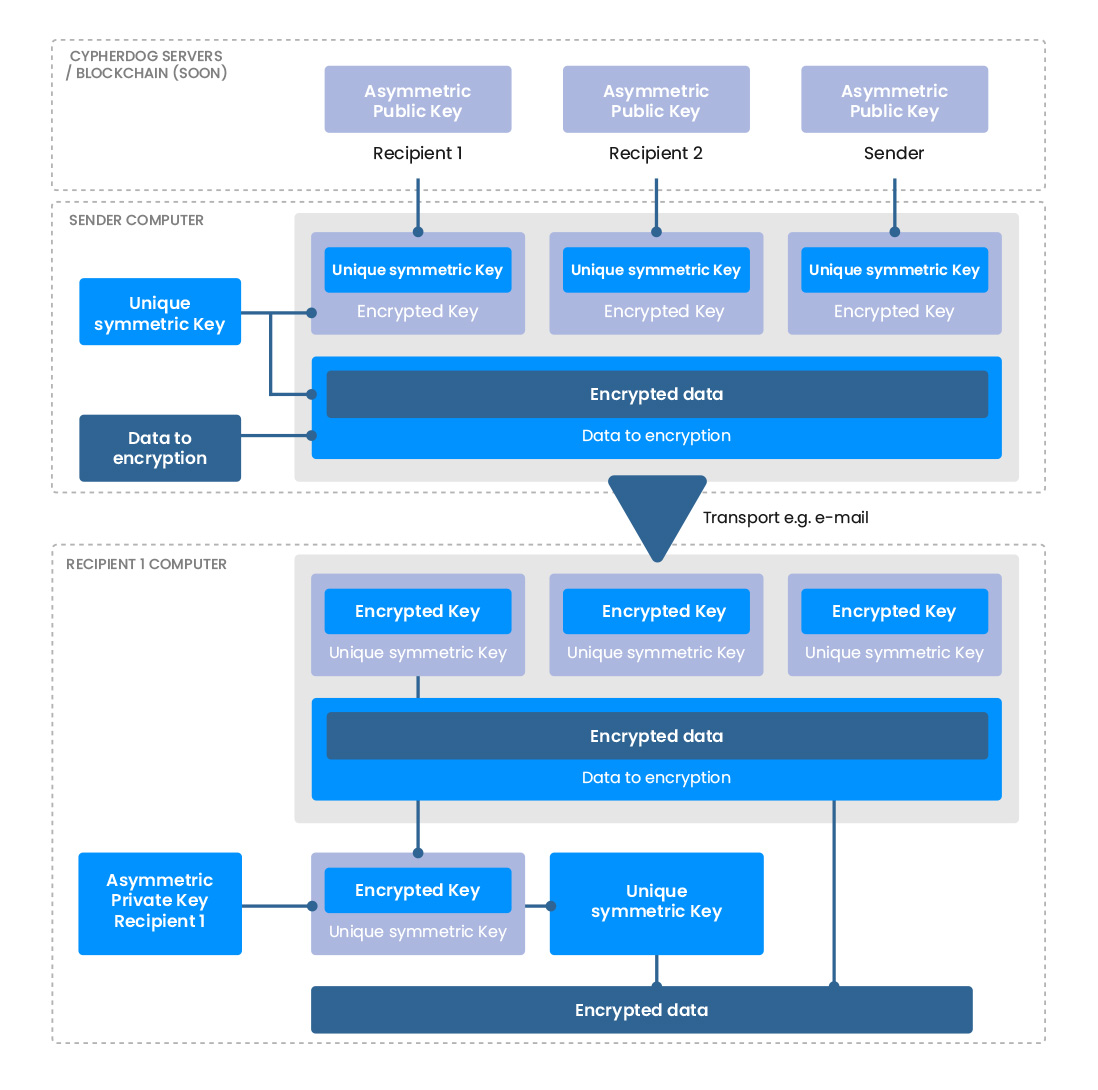
Cypherdog Encryption Architecture
The Cypherdog desktop application is compatible with all modern operating systems like Windows, macOS, and Linux
To simplify encryption and decryption of e-mails, you may opt to install the plugin for Gmail & Google Suite
for any of the three top browsers (Chrome, Firefox, Edge) or add-ins for Outlook and Thunderbird.
Two modules of the solution
Cypherdog Encryption Application
an application installed in the operating system, available from the sidebar
Cypherdog Encryption Plugin
a plugin installed in a browser or
e-mail native client
The Cypherdog Encryption Plugin module is responsible for interacting with the user and managing the encryption and decryption of messages. The Cypherdog Encryption Application module, on the other hand, supervises the authorisation to your private key and performs cryptographic operations in a tangible sense.
Only processes authorized by the Cypherdog Encryption Application module can use your private key. This means that the browser and other approved methods will never have control over your private key. They will only be able to use it to encrypt and decrypt messages. The architecture of our solution ensures complete separation of customer's e-mail from your private key.

Cypherdog uses proven cryptographic algorithms, such as the 3072-bit RSA key and the SHA512 hash function. Furthermore, its system architecture is designed to be adaptable to the challenges of the future. This involves accommodating external suppliers in the user identity verification process, implementing the system within blockchain frameworks, and exploring hardware wallet solutions.
Features

End-to-end encryption
Cypherdog Encryption is based on a combination of asymmetric and symmetric encryption. No one can decrypt files without the unique private key stored in the recipient's Cypherdog application.

No trusted third party
Cypherdog, third party organizations and providers, e.g. e-mail services, file sharing providers or Certification Authorities, are excluded from the encryption and decryption processes and have no ability to access any data.
Independency on transport layer
Cypherdog Encryption allows you to encrypt any text or file and send it using various communication channels, such as e-mail, file-sharing platforms like Google Drive, Dropbox, or Microsoft OneDrive, as well as instant messenger platforms like Telegram, Signal, WhatsApp, and other methods like WeTransfer.

Independency on e-mail provider
Cypherdog Encryption is compatible with all e-mail providers and clients. We support the use of plugins, such as Gmail, Outlook and Thunderbird. However, if you prefer to use another e-mail application, you can always use a “magic window” to encrypt and decrypt messages.

Protection of internal and external communication
Cypherdog Encryption enables organizations to protect their communication processes, including outgoing e-mails, chats, and file transfers through any other sharing platform.

No provider access
Cypherdog, as a service provider, does not have any access rights to data. When using any communication channel to share content, neither Cypherdog nor the provider have access to decrypted files and texts in any form.

Zero-knowledge security model
The service provider cannot recover your encrypted data or access your account in case you lose your private key, its backup, or the password needed to decrypt it. The use of zero-knowledge security guarantees complete data confidentiality and privacy.

Absolute protection of the private key
When you log in to the application for the first time, a private key is generated that only you, as the user (either a company or an individual), have access to. If the private key becomes lost or inaccessible, it cannot be recovered, ensuring that it remains solely in your possession and is not accessible to anyone else.

Anonymization and metadata collection
We do not collect additional data about our users, such as IP number, geographical location, logs, mobile phone numbers, and connections between users. We only know one thing - the user's e-mail, which is his ID.
How we encrypt your data