
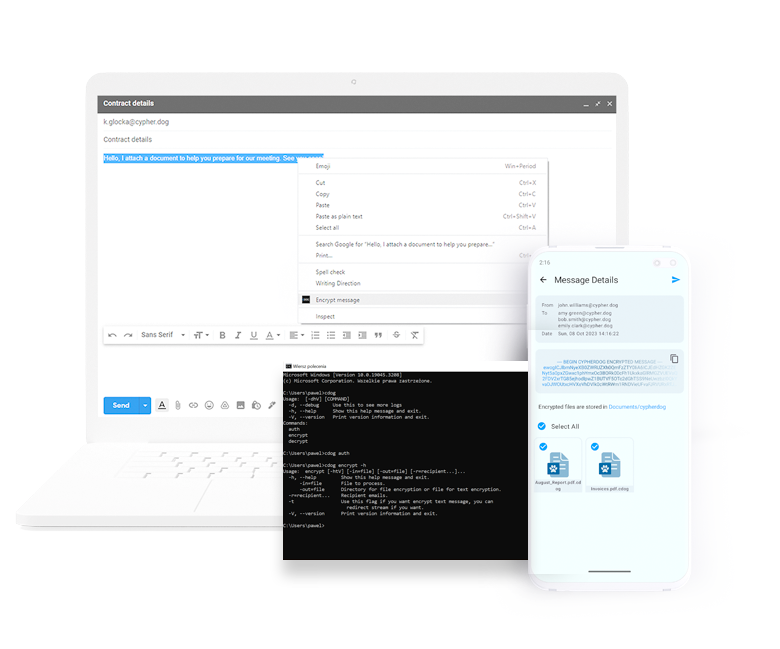
How it works
One-click. Complete protection. Cypherdog Encryption allows you to encrypt and decrypt any text or file and send them using any media, including e-mails supported by plugins to Firefox, Chrome and Edge browsers, Gmail/Google Suite, AddIns in Outlook and Thunderbird.
You can send and receive encrypted files and messages using any web client or native e-mail client or Slack, WeTransfer, Google Drive, or any other communication method. You are always assured that only the authorized recipient will have access to the decrypted content.
The software allows for bulk encryption and decryption of files or texts via command-line interface, enabling its use by organizations sending multiple encrypted documents to their counterparts, such as banks or medical diagnostic stations.
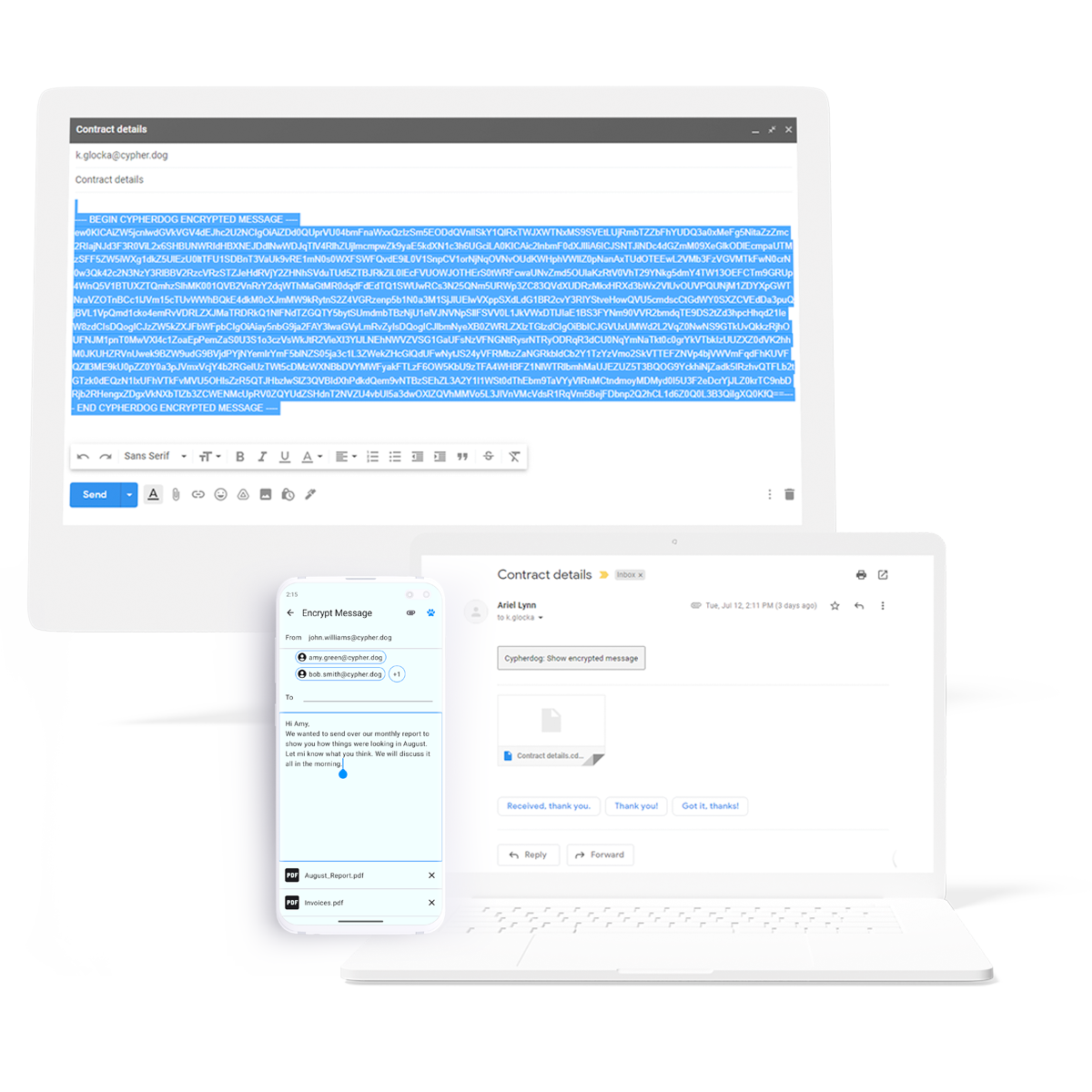
Threats in cyberspace
E-mail is one of the most popular electronic communication channels. Like most digital services, it is vulnerable to cyberattacks, which may result in unwanted access to your mailbox and disclosure of confidential information. In the event of unauthorized use of the compromised mailbox, message recipients cannot confirm the sender's identity.
Activities such as file transfer, file sharing, or messaging are susceptible to cyberattacks, often resulting in the leakage or theft of data for the purpose of economic espionage or compromising the organization. Invoice hacking and ransomware are the most rampant and dangerous cyber threats existing today. Cypherdog Encryption provides a solution to combat them.
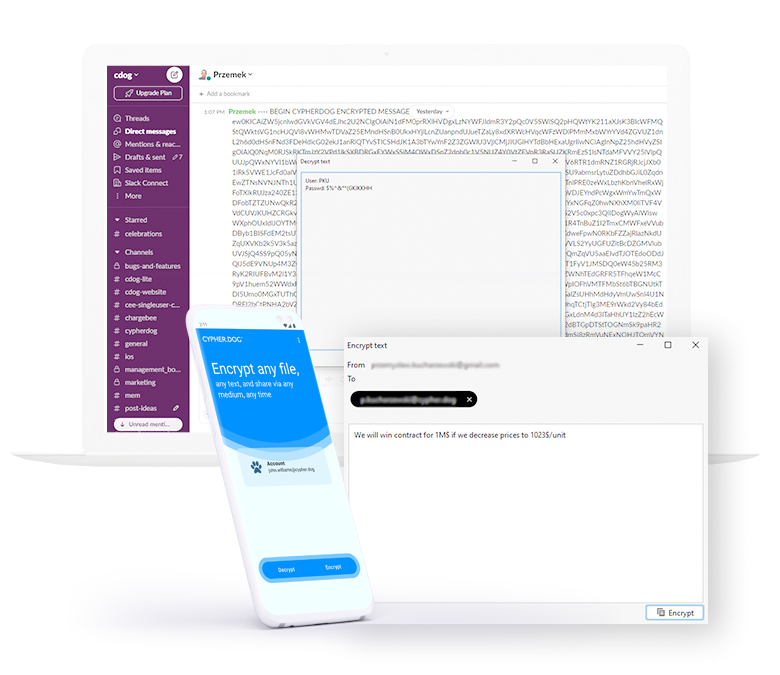
Security
Cypherdog Encryption is based on a combination of asymmetric (RSA3072) and symmetric (AES-256) encryption. There is no “trusted” third party in our solution, including us, no Certification Authority and no other communication channel provider (e.g. e-mail service provider). We do not have access to data encrypted by users because we do not have access or copies of the private keys needed for decryption.
Cypherdog Encryption is a comprehensive solution: on the one hand, it provides encryption of messages and keeping their contents undisclosed to unlawful users; on the other hand, it allows the recipient to confirm the sender's identity.
Cypherdog Encryption supports GDPR, DORA, NIS2, and ISO 2700x implementations and other regulations.
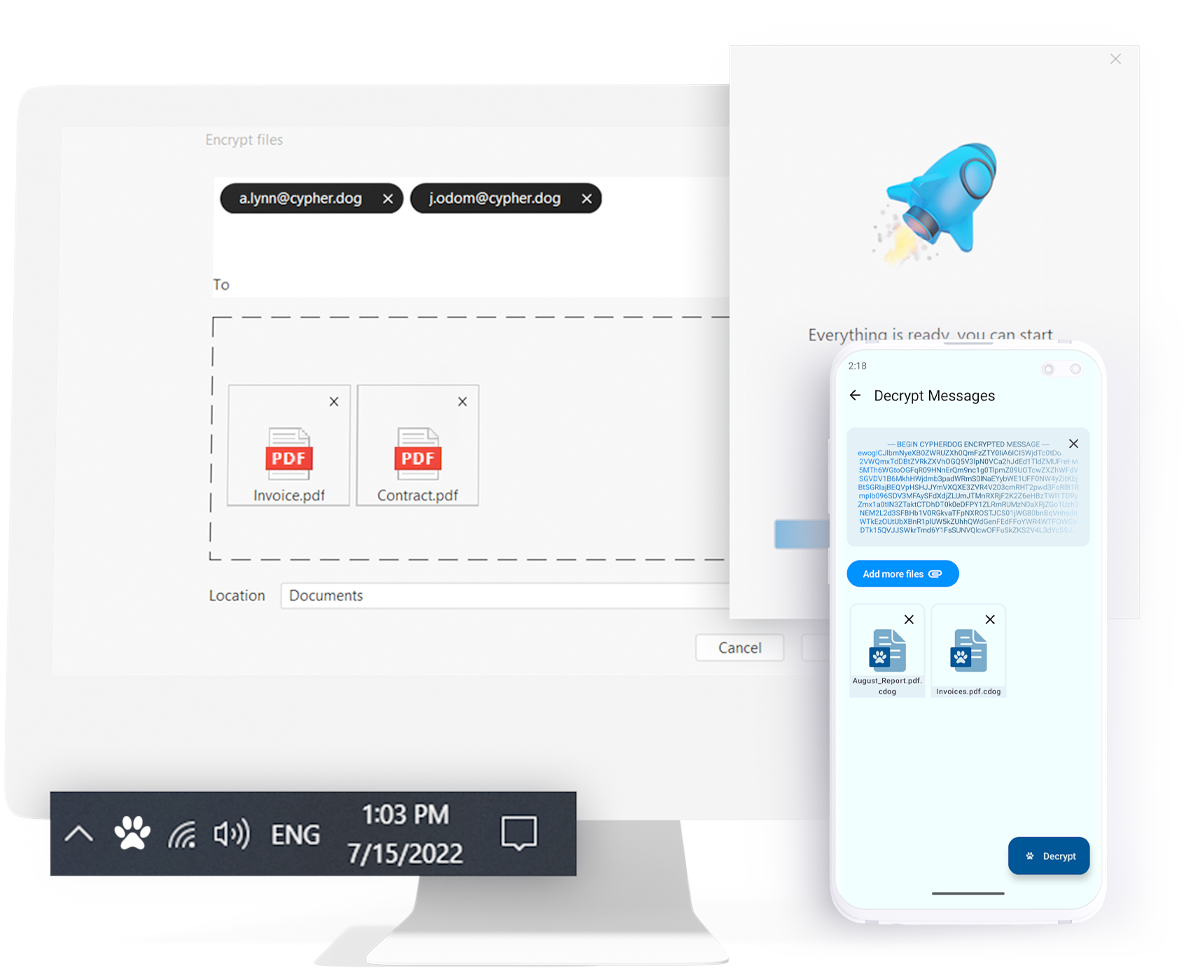
Friendly user interface
Cypherdog Encryption software focuses on simplicity and ease of use. Its Installation process and user registration system are so simple that any individual who has experience with installing antivirus software should be able to handle it without difficulty.
You can encrypt a file by right-clicking and selecting the recipient. You can decrypt a file simply by double-clicking on the file icon. E-mail messages can be partially or fully encrypted by right-clicking on the selected text. Decryption is straightforward and requires only clicking on a button or link, without sharing any passwords or codes with other parties. Cypherdog Encryption, once installed, is all that is needed.
| Cypherdog Encryption specifications | Free mobile | Free desktop (after trial) | Single User & Trial | Business |
|---|---|---|---|---|
| Text/e-mail messages encryption | ✓ | - | ✓ | ✓ |
| Encryption of files/attachments in e-mail messages | ✓ | - | ✓ | ✓ |
| Decryption of e-mail messages/ texts and attachments/ files | ✓ | ✓ | ✓ | ✓ |
| Administration panel for users & private keys management | - | - | - | ✓ |
| Backup private key to file (on device) | ✓ | ✓ | ✓ | - |
| Backup of private key to company server in Vault | - | - | - | ✓ |
| One license key for a single user | - | - | ✓ | - |
| One license key for multiple users | - | - | - | ✓ |
| Basic support and online training | ✓ | ✓ | ✓ | - |
| Advanced support and training | - | - | - | ✓ |
| Command line text/file encryption/decryption | - | - | ✓ | ✓ (scalable) |
| Cooperation with security systems on gateway | - | - | - | ✓ |
| E-mail aliases | ✓ | ✓ | ✓ | - |
| Cryptography | Encryption: asymmetric RSA3072 and symmetric AES-256, SHA512 hash function | |||
| Microsoft Outlook | supported | Add-ins to Outlook 2016+ for Microsoft 365/ Exchange Server, webclient & native | ||
| Gmail | supported | Plugins: Google Chrome, Microsoft Edge, Mozilla Firefox | ||
| Mozilla Thunderbird | supported | Add-ons for Thunderbird for all e-mail providers and servers | ||
| Other e-mail clients | all supported | Manual encryption / decryption / right-click or “magic window” | ||
| Other communication channels | all supported | WeTransfer, Slack, Google Drive, Dropbox, WhatsApp, Messenger etc. | ||
| Operating systems | iOS/Android | Windows, macOS, Linux + free mobile app (iOS, Android) | ||
Pricing
Free desktop
free
$ 0 / user / year
Single User features in the first 14 days, after this period only decryption function
DownloadSingle User
for SOHO & SME
$ 60 / year
After 14 days without a license code, it goes to the Free version
Try for freeBuy nowBusiness
Book consultationFree desktop
free
$ 0 / user / month
Single User features in the first 14 days, after this period only decryption function
DownloadSingle User
for SOHO & SME
$ 6 / month
After 14 days without a license code, it goes to the Free version
Try for freeBuy nowBusiness
Book consultationAdvantages
You can encrypt, send and decrypt messages received with one click.
The only thing you need to perform the encryption operation is the recipient's e-mail (the recipient must also use the Cypherdog application).
You can be sure that the sent message will remain confidential (a third party cannot read it).
The message can be read only by you and the indicated recipient.
Recipient can confirm that you are the sender of the message.
You can send messages to many recipients at the same time.
You can encrypt any text not only in the e-mail program but also in documents, presentations, sheets or text files.
The software also enables the encryption of entire files.
Your cryptographic keys never leave your computer and, in the event of their loss, you can recover them from a USB backup or printout.
If you use multiple devices, you can transfer cryptographic keys from one device to another.
The unique architecture of the solution ensures the security of your cryptographic keys (e-mail programs cannot read them but only use them to encrypt and decrypt messages).
Testimonials
“Cypherdog Encryption is an intuitive and easy to implement solution that from day one allows us to safely exchange information and files both within and beyond the organization. With its integration on Windows, MacOS and Linux, it utilises efficiently its capabilities even in diverse environments.”
— Piotr Mrowiec, Security Systems Engineer
Net Complex - July 6, 2023
"I like the asymmetric encryption that it provides in this segment. It protects our vital data from cyber attacks. Easy to encrypt and decrypt email including attachments very easily and without any hassle. It offers data privacy and data leak protection at very reasonable pricing. User community is very huge due to its trust. Easy to deploy and works well on all Operating Systems like Mac, Windows and Linux. Customer support is always available and ready to help the users at any time."
— Nikita S. - February 26, 2023
"Cypherdog Encryption is a very effective and advanced solution that protects emails in Microsoft Outlook and Gmail. It is a nice and recommendable application that offers data privacy protection and it's very easy to encrypt attachments and email messages. Very easy to install, set up and get started with so no training is needed."
— Maxwel J. - November 7, 2022
"This tool is necessary to all businesses to ensure they have protection from external attacks and all sensitive company information is safeguarded. They have detailed documentation and videos to help you with installation and how to use it. It is simple to use and offers total protection to your emails."
— Benson K. - November 7, 2022
"Cypherdog Encryption offers outstanding protection for sensitive information because of its automatic encryption, simplicity of use, and zero-knowledge architecture. Strongly advised for anyone worried about their privacy online."
— Nazim - Reviewed March 2023
"Cypherdog Encryption is a very interesting solution that, on the one hand, allows you to protect the confidential data sent within the company, and can also be used as security when sending valuable documents from the entrepreneur’s point of view to customers and partners outside the company. Due to the combination of a high level of security and ease of configuration and use, it is also used in the micro and SME sector without dedicated IT departments and in large organizations with global IT support."
— Maks Kisyk - CEO, BF Group
"Cypherdog Encryption is one of the most secure solutions for confidential communication. In my opinion, the most important features are absolute private key protection, zero-knowledge security method, and no “third party.” In my opinion, it is an ideal solution for those who want to maintain the highest confidentiality of communication and have a manageable tool for confidential communication via email."
— Artur Markiewicz - Cybersecurity Consultant
"A great solution for companies in the SMB sector, because it requires very little IT facilities and provides benefits in areas that non-technical people can understand. Cypherdog Encryption is a very good solution from the point of view of implementation and ease of use by the end user."
— Alex Sawsienowicz - User Experience in Venafi, USA












